An Introduction to Tcpdump
If you are an avid Linux user, chances are you’ve heard of Tcpdump. This powerful utility, which uses the libcap library for packet capturing, is often used by network engineers and administrators as a troubleshooting tool. To use Tcpdump, however, you need superuser privileges. Let’s take a closer look at what Tcpdump can do and how to get started using it.
What Can Tcpdump Do?
Tcpdump is a powerful utility that can be used to capture and analyze packets on network interfaces in Linux-based operating systems. It can be used to diagnose problems with your network or even detect malicious activities occurring on the same network interface. For example, if you suspect that someone is using your Wi-Fi without permission, running tcpdump will allow you to view all of the packets being sent over the interface and determine if someone else is indeed connected without authorization.
How To Execute Tcpdump?
The first step in using tcpdump is to make sure that you have superuser privileges.
From the terminal we need to run the following command:
Basic Syntax: tcpdump -i [interface] > [output filename]
In addition to this basic command syntax, there are several other options available for more advanced usage of tcpdump such as filtering traffic based on port numbers or IP addresses as well as setting up alerts when certain types of traffic are seen on your network. Before attempting these more advanced operations though, it's best to familiarize yourself with the basics first by running tcpdump with its basic command syntax described above.
Typical tcpdump output format
Sample output:08:39:05.562326 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 2828785530:2828785738, ack 3051976676, win 442, length 208
Timestamp of when the libcap packet was picked up, in milliseconds or microseconds.
Protocol-specific information.
Source IP and source port of the packet.
Destination IP and destination port of the packet. 5. Following that, TCP flags like SYN, ACK, FIN, RESET, and URGENT [all represented by their first letter except for ACK, which is represented by a dot(.)]
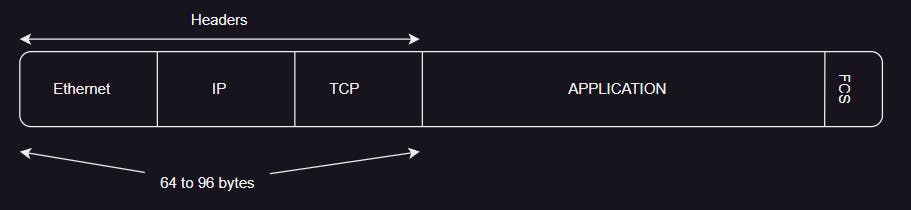
Network packet stucture
A network packet is typically composed of the following partitions:
TCP dump command different options examples:
- To continuously capture packets on all interfaces, use the following command. Note that you will need to press ctrl + c to force stop the process:
tcpdump -i any
- To capture packets on all interfaces, use the -c option with a value of 5. This will limit the number of packets captured to 5 and stops the capture process.
tcpdump -i any -c 5
Output:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
08:17:42.358148 IP some-hostname.ssh > 10.02.1.27.52168: Flags [P.], seq 2828779978:2828780186, ack 3051974884, win 449, length 208
08:17:42.358685 IP some-hostname.22907 > another-hostname.domain: 33427+ PTR? 227.105.74.10.in-addr.arpa. (44)
08:17:42.359752 IP another-hostname.domain > some-hostname.22907: 33427 NXDomain 0/1/0 (112)
08:17:42.360002 IP some-hostname.ssh > 10.02.1.27.52168: Flags [P.], seq 208:432, ack 1, win 449, length 224
08:17:42.360087 IP some-hostname.ssh > 10.02.1.27.52168: Flags [P.], seq 432:816, ack 1, win 449, length 384
5 packets captured
5 packets received by filter
0 packets dropped by kernel
- The tcpdump utility will run reverse dns look ups to find hostnames for ip addresses. Without the -n option, tcpdump utility will create extra traffic this way.
tcpdump -i any -c 5 -n
output:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
08:22:10.563919 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 2828782970:2828783178, ack 3051976532, win 442, length 208
08:22:10.564134 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 208:400, ack 1, win 442, length 192
08:22:10.564229 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 400:576, ack 1, win 442, length 176
08:22:10.564310 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 576:752, ack 1, win 442, length 176 08:22:10.564389 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 752:928, ack 1, win 442, length 176
5 packets captured
5 packets received by the filter
0 packets dropped by kernel
- We can configure the packet size captured by tcpdump, and we can check the capture size in the second line of output. This lets us know how much data is being captured and helps us optimize our settings.
tcpdump -i any -c 5 -n -s96 [Limiting the data packets to 96 bytes]
The size of the packets that tcpdump captures can be configured by using the -s option. The size is usually based on what we need to use tcpdump for.
For example:
If we just need to find evidence of lost or out-of-order packets, then 64 or 96 bytes should be sufficient.
If we are troubleshooting issues at the application level, then we may need to capture the full packet. In such cases, 65,000 bytes should be plenty.
If the capture size is set to 96 bytes, this will only capture the headers.
listening on any, link-type LINUX_SLL (Linux cooked), "capture size 262144 bytes"
The default capture size for each packet in tcpdump is 262144 bytes, but this can be changed to be as small as 96 bytes.
Output:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 96 bytes
08:39:05.562326 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 2828785530:2828785738, ack 3051976676, win 442, length 208
08:39:05.562531 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 208:400, ack 1, win 442, length 192
08:39:05.562608 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 400:576, ack 1, win 442, length 176
08:39:05.562685 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 576:752, ack 1, win 442, length 176
08:39:05.562753 IP 10.15.1.27.ssh > 10.02.1.27.52168: Flags [P.], seq 752:928, ack 1, win 442, length 176
5 packets captured
5 packets received by filter
0 packets dropped by kernel
- We can check DNS traffic by using UDP port 53 [default port DNS looks up will use]
tcpdump -i any port 53 -n
A? -> ipv4 and AAAA? -> ipv6 in the output:
Terminal-one:
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on any, link-type LINUX_SLL (Linux cooked), capture size 262144 bytes
09:09:15.351685 IP 10.02.1.27.49155 > 10.15.1.27.domain: 24755+ A? logging.example.com. (61)
09:09:15.352730 IP 10.15.1.27.domain > 10.02.1.27.49155: 24755 4/13/6 CNAME example.com., A 12.14.13.19, A 19.16.14.26, A 19.16.12.25 (488)
09:09:15.352781 IP 10.02.1.27.49155 > 10.15.1.27.domain: 64700+ AAAA? logging.example.com. (61)
09:09:15.353709 IP 10.15.1.27.domain > 10.02.1.27.49155: 64700 1/1/0 CNAME example.com. (159)
09:09:28.015153 IP 10.02.1.27.48947 > 10.15.1.27.domain: 6226+ [1au] A? telementry.example.com. (77)
09:09:28.015208 IP 10.02.1.27.60452 > 10.15.1.27.domain: 41913+ [1au] AAAA? telementry.example.com. (77)
09:09:28.016102 IP 10.15.1.27.domain > 10.02.1.27.60452: 41913 1/1/1 CNAME telementry.igenstion.example.com. (202)
09:09:28.016185 IP 10.15.1.27.domain > 10.02.1.27.48947: 6226 10/13/10 CNAME telementry.igenstion.example.com., A 10.1.6.30, A 19.14.14.11, A 12.34.5.233, A 11.23.2.32, A 22.1.6.42, A 2.4.13.12, A 32.45.14.23, A 13.91.4.123, A 12.4.4.12 (711)
Terminal- two:wget example.com
- To capture and save the packets into a file for later analysis:
tcpdump -i any -w capture.pcap
Capture packets/traffic for specific source IP address and specific destination port
tcpdump -nnvvS src {ip-address} and dst port 8080 -w capture.pcap
With this command, traffic originating from the src IP address and sent to port 8080 will be captured, where a client will read it.